As businesses embrace the Internet of Things (IoT) to enhance operations and boost efficiency, the security of these IoT-enabled devices is more critical than ever. IoT environments — from smart sensors to industrial machinery — become increasingly vulnerable to cyber attacks, data breaches, and unauthorized use. Without robust security measures, organizations stand to lose a great deal, including funds, operational disruption, and reputation loss. Overcoming these challenges head-on is essential to protecting sensitive data, maintaining system integrity, and realizing long-term success in an increasingly interconnected world.
What is IoT Security?
IoT (Internet of Things) allows devices to be connected to the internet, facilitating data exchange and automation. IoT security defends the devices from cyber attacks, guaranteeing data privacy, device operation, and system integrity. Incidents have to be avoided, sensitive data has to be protected, and trust has to be gained as more industries such as healthcare, manufacturing, and smart homes become dependent on connected technology.
The Importance of IoT Security
Since more companies are turning to IoT for automating and upgrading services, security is vital. A compromised IoT system can cause lost data, functionality impaired, money lost, and reputation lost. Above all, industries like healthcare, manufacturing, and agriculture depend on IoT to provide peak performance — that is, all weaknesses will have actual effect. Robust IoT security ensures data integrity, blocks unauthorized access, and supports long-term scalability of secure connected IoT devices.
Top IoT Security Challenges

- Device Vulnerabilities: Security is not a built-in feature of most secure IoT devices, an easy target for any hacker. Functionality stands above security while manufacturing, and such devices become vulnerable to hacking.
- Weak Authentication: Weak or default passwords provide unauthorized entry to devices and networks. The attackers exploit these vulnerabilities and gain access to entire IoT ecosystems.
- Data Breaches: Data sent among devices and the cloud could be intercepted and hacked if not encrypted. This results in economic loss, identity theft, or industrial espionage.
- Lack of Updates Over Time: The majority of the secure IoT devices are not designed with constant security patches, so they remain exposed. It makes them a target, a constant flaw that is exploited again and again by the hackers.
- Botnet Attacks: Hackers hijack vulnerable IoT devices, forming large networks (botnets) to launch Distributed Denial of Service (DDoS) attacks, causing massive downtime and disrupting business operations.
- Privacy Concerns: Personal and business data captured by IoT sensors can be intercepted or hacked without proper security solutions. Aside from being an invasion of privacy, it can also lead to lawsuits and loss of consumer confidence.
Best Practices to Overcome IoT Security Challenges
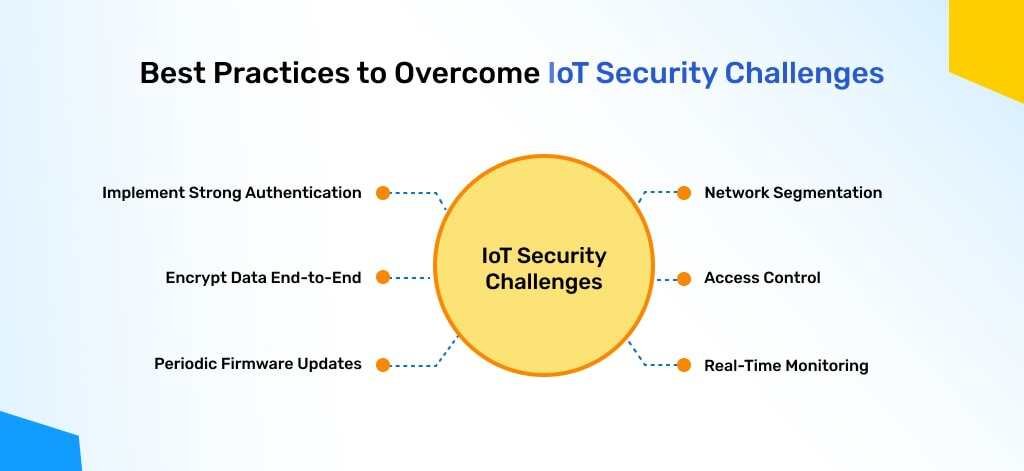
- Implement Strong Authentication: Implement multi-factor authentication (MFA) and require strong, unique passwords for all IoT cybersecurity devices. Incorporate biometrics or hardware tokens for additional security.
- Encrypt Data End-to-End: Encrypt data that rests and data that is moving in order to ensure security against unapproved entry. Use of stringent encryption principles (AES-256) brings more security into data.
- Periodic Firmware Updates: Update device firmware periodically to resolve vulnerabilities and enhance performance.
- Network Segmentation: Network segmentation separates IoT devices on a standalone network from core systems, minimizing the attack surface and isolating potential breaches to keep hackers from accessing core business infrastructure.
- Real-Time Monitoring: Install AI-based threat detection systems to scan traffic patterns and mark malicious activity. Always-on monitoring makes it possible to respond promptly to anomalies and potential breaches.
- Access Control: Limit user access to only the most critical functions, and reduce the risk of insider attack. Use role-based access control (RBAC) to grant users only the necessary permissions.
The Future of IoT Security: What’s Next?
The future of IoT cybersecurity challenges will be automation, AI, and regulation. Threat detection will be made smarter through machine learning algorithms, recognizing patterns at a rate that’s higher than what current methods can accomplish. Edge computing will cut back on sending data to central servers, which lowers the IoT risk management. Also, IoT security global regulation will make companies prioritize built-in security. Blockchain technology will perhaps help secure device-to-device communication and maintain data integrity.
How Hutech Solutions Empowers Businesses to Overcome IoT Security Challenges
Hutech Solutions enables companies to address IoT security issues through customized, end-to-end protection strategies.
- Custom Security Solutions: We offer security solutions specific to your own IoT infrastructure.
- Advanced Threat Intelligence: Utilizing AI and machine learning, we are always monitoring devices in real-time for suspicious activity and potential breaches.
- End-to-End Encryption: We encrypt data from collection to storage.
- Device Lifecycle Management: From installation to retirement, we have devices updated, kept in check, and retired securely.
- Compliance Assistance: We assist companies in adapting with changing IoT security legislation to prevent fines and protect business operations.
Secure your IoT environment from cyber attacks – Trust Hutech Solutions to protect your devices, information, and operations with innovative security solutions. Contact now and future-proof your company!
The Future of Secure Online Payment Gateways in E-commerce
The future payment gateway is being revolutionized with the arrival of AI, blockchain, and biometric authentication. AI-powered fraud detection, decentralized payment platforms, and tokenized digital transaction safety are becoming mainstream. Moreover, additional regulatory demands will compel companies to follow more rigorous security protocols. With digital transaction safety on the rise, payment gateways will become the linchpin for e-commerce security.
Conclusion
The more IoT usage expands, greater the security challenges that come along with it. From device attacks to data intrusion, businesses must actively protect their IoT network security and data. Having good security systems in place and working with experts like Hutech Solutions can assist in keeping IoT investments secure, dependable, and groundbreaking.
Since secure IoT devices are evolving each day, being ahead of the attacker is now not an option, it is an imperative. Businesses that undertake prudent IoT security challenges practices today will build more secure, agile, and competitive organizations tomorrow.
Ready to Advance your Digital Transformation?Get in touch with us.
Discover why Hutech is the right partner for your business.
MAIL US AT
sales@hutechsolutions.com
CONTACT NUMBER
+91 90351 80487
CHAT VIA WHATSAPP
+91 90351 80487
Humantech Solutions India Pvt. Ltd 163, 1st Floor, 9th Main Rd, Sector 6, HSR Layout, Bengaluru, Karnataka 560102




